Jdlib a Java Wrapper for Dlib library
- 2020-12-30
- Taha Emara
- Dlib, Jdlib, Face Recognition, Face Clustering, Java
In this post, I introduce Jdlib a java wrapper for Dlib toolkit.
How to build a custom object detector using Yolo
- 2018-07-31
- Taha Emara
- Deep Learning, Deeplearning4j, Computer Vision, Yolo, Java, Object Detection
In this post, we will learn how to build a custom object detector using Yolo. For example, I made a detector to detect my Rubik’s Cube.
Real-time Sudoku Solver
- 2018-05-19
- Taha Emara
- Computer Vision, Deep Learning, Machine Learning, Deeplearning4j, Opencv, Java
In this post, we will learn how to solve a printed sudoku solver using a real-time feed from a camera.
Real-time Distance Measurement Using Single Image
- 2018-03-11
- Taha Emara
- Opencv, Java, Computer Vision
In this post, we will learn how to develop an app to measure a distance between a pinhole camera and an object.
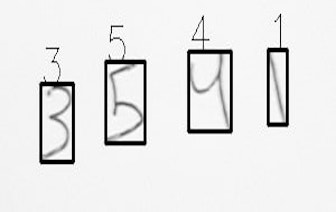
Handwritten Multi-digit String Segmentation and Recognition using Deep Learning
- 2018-02-17
- Taha Emara
- Opencv, Machine Learning, Deeplearning4j, Deep Learning, Java
In this post, we will learn how to develop an application to segment a handwritten multi-digit string image and recognize the segmented digits using deep learning.
Arabic Handwritten Characters Recognition using Deeplearning4j
- 2017-10-18
- Taha Emara
- Deeplearning4j, Machine Learning, Java, Deep Learning
In this post, I introduce an implementation of a proposed CNN design for Arabic handwritten characters recognition.

How to use Weka in your Java code
- 2017-07-02
- Taha Emara
- Machine Learning, Java
In this post, I will explain how to generate a model from ARFF dataset file and how to classify a new instance with this model using Weka API in Java.
Object recognition using TensorFlow and Java
- 2017-04-29
- Taha Emara
- Machine Learning, Java
Using TensorFlow and Inception-v3 model, I built this small demo in Java to recognize objects in images and classify it into 1000 classes like Lion, Frog, Flowers, ....etc.

Implementation of classical encryption techniques in Java
- 2017-03-23
- Taha Emara
- Programming, Java, Security
In this post, I will explain classical encryption techniques Ceasar cipher, Monoalphabetic cipher, and Playfair cipher, and provide a java code demonstrating encryption and decryption processes for each one.
End to End Voice Encryption between Raspberry pi and PC using AES
- 2016-08-05
- Taha Emara
- Security, Java, Raspberry Pi
The value of encryption increases over time simply because encryption keeps your call from eavesdroppers and protects confidential data, Obviously it shows more value when it comes to military or financial affairs.

Builder pattern in Java
- 2016-05-24
- Taha Emara
- Java, Programming
Design pattern is best practise and a proper solution to a problem faced by software developers this solution based on two principles of object oriented design . 1- Program to an interface not an implementation. 2- Preferring object composition over class inheritance.

Introduction to Redis database and using it with Java
- 2016-01-23
- Taha Emara
- Java, Database
More speed is a dominant need in our life and IT field has no exception from that. Redis comes to meet the need of speed in the database domain.
